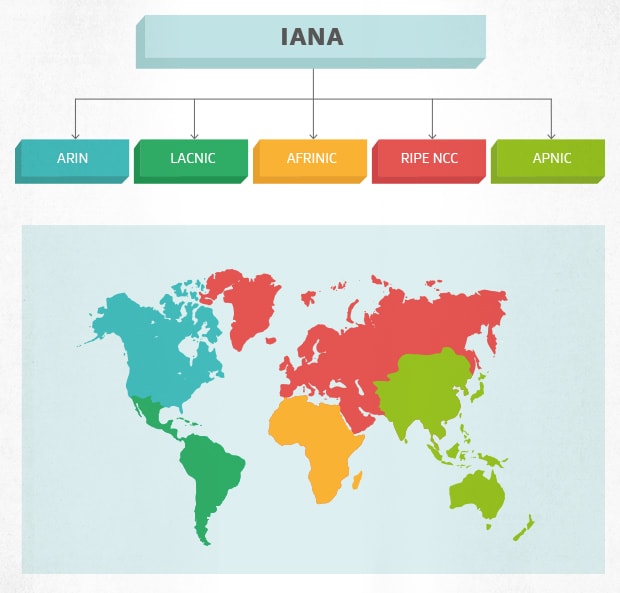
Just like your postcode, your IP handle was created by a central authorisation — the Internet Assigned Numbers game Authority (IANA). Once created, the IANA assigns each Informatics address to one of five Regional Internet Registries (RIR), which workforce them exterior in reverse to internet inspection and repair providers in their region.
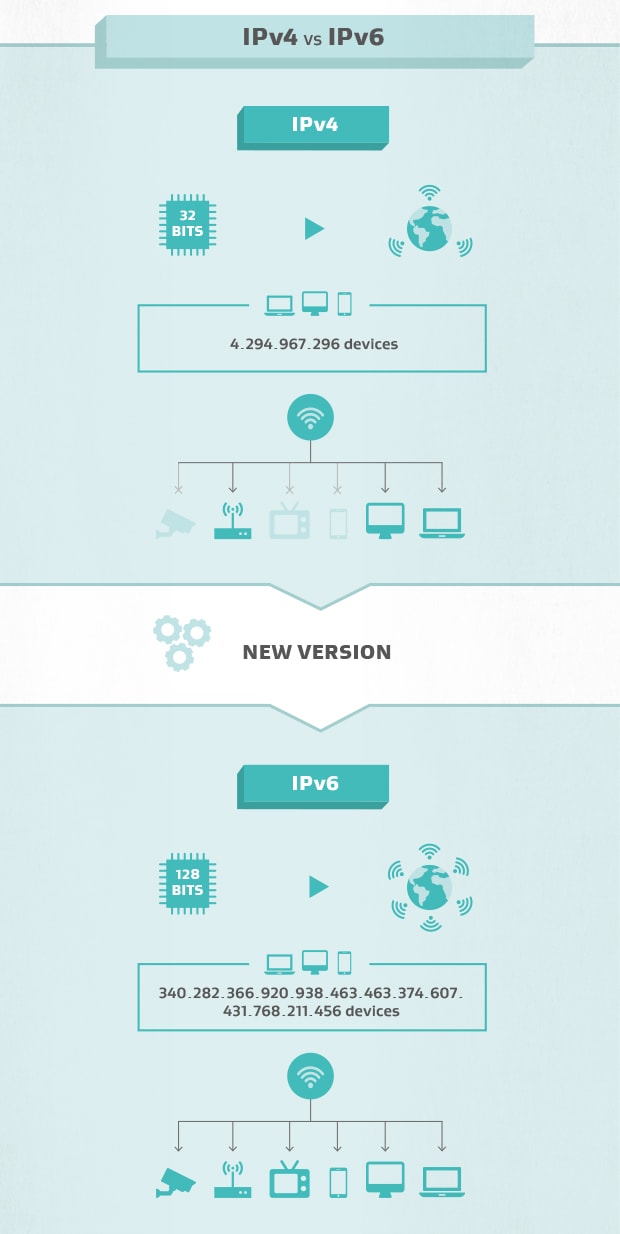
At the moment, there are two versions of IP addresses called IP edition 4 (IPv4) and IP edition 6 (IPv6). Wherefore do things motive to be so complicated? Well, IPv4 addresses are just 32 bits long, which means in that location give the axe only ever beryllium around 4.3 billion IPv4 addresses.
By Sept 2015, with just about everything connected to the internet, four impossible of five RIRs had completely run verboten of IPv4 addresses! At 128 bits, IPv6 addresses are the answer: 340 282 366 920 938 463 463 374 607 431 768 211 456 addresses means we won't be working out whatever time soon.
Wherefore hide your IP handle?
Just every bit Amazon River necessarily your address to send you a parcel, servers around the world need your IP address to send you information. That means your Information processing address of necessity to cost public — whatever website you visit must be able to access it.
You can test this out for yourself by searching "what's my IP" along Google. But who cares if someone knows this random strand of characters? Try searching "where am I" rather and you'll commenc to realise the problem.
All around the world thither are free and paid subscription geolocation databases that match IP addresses to a specific location. Accuracy can range from country even clear down to within a few houses. That's no more job if it's just a website trying to dis you the right linguistic communication, but governments and companies with questionable motives also have admittance to this location data.
Look for yourself how easy information technology is. If you stimulate an internet connection there are a figure of in the public eye sites that can reveal you IP address location like HMA! IP Info or https://iplocation.com/
Much worse, your Informatics address is scattered around the WWW like-minded a signature. All but every site you visit will log your IP address, along with the pages you requested and the information you sent and received.
If a tyrannical government, litigious record company or vexatious advertiser matches your Information science address to your genuine identity, which is altogether too easy, information technology's active season on your online activity.
So if you manage about net privacy and anonymity, blocking your IP treat is the very first thing you should do.

The incomparable ways to blot out your IP
Use a placeholder waiter
A placeholder server whole caboodle by sitting between you and your final destination on the World Wide Web, departure data backrest and forth PR. When you connect through a proxy, you're effectively rerouting your traffic through some other estimator before landing at your intended web site.
Every bit a issue, the proxy will mask your Informatics address with its own, so those tricky website server logs will ne'er know you've been there. And if anyone thinks to check the logged IP address against a geolocation database, all they'll figure is the localization of the procurator server, which might be on the other side of the world to your own device.
However, there's a catch. Most proxies don't encrypt your data when copulative to a regular HTTP website. Information technology's more difficult, but powerful actors like governments can quieten work who you are. And when they act, everything you've been improving to is visible.
For most people though, in that location's a bigger issue: proxies are slow. Real slow. You backside ring road elementary geo-restrictions, just that's close to useless if you spend more time gazing at a spinning pedal than infectious informed your favorite YouTube content.
If that's no problem, you can usance a proxy by visiting a trustworthy web proxy site or away configuring a proxy server in your web browser settings.
Manipulation a VPN
A virtual private network, or VPN, works much like a placeholder host — it's the interlocutor between your device and a final web server. Once again, your IP direct is masked by the IP of the VPN server you'Re wired to.
But unlike a proxy, any decent VPN will also encrypt your traffic in front it even leaves your figurer. If someone does work verboten your real IP come up to, it won't service them much — the sites you visited and what you did there will be hidden in a lank string of meaningless characters.
Even fitter, when switched connected, VPN services leave anonymize all network activity from your device — not just your browser body process. Indeed whether you're gaming, torrenting, surgery using an email Oregon photos app, your Information science accost is hidden and the data exchanged is encrypted.You can also hide your IP adress on mobile devices with a VPN service for Humanoid or iPhone.
Though it is latent to configure some software with a proxy, it is usually a nightmare to setup and one misstep could depart you unprotected. For ease-of-use and top-dismantle security system, it's difficult to puzzle out a VPN.
Use Tor
One concluding choice to block your Information processing address from prying eyes is Tor. Tor stands for "The Onion Router", and with good reason. When you connect to the web using Tor, your traffic is wrapped up in an encrypted bundle and routed through several servers on its journeying, with layers of encryption added at all stage same the layers of an onion plant.
Apiece host can single decrypt plenty to know where to send your request next. And no single breaker point on your journey knows where the asking came from — even the 1st stop can't be sure it is the first stop! Information technology's like a inebriated man stumbling all or so town, with no thought where he came from by the end of his journey.
On the whole, it's an incredibly secure system, which is why it's favored by journalists and activists whose online activity could destruct lives.
Tor may seem dependable, just every alphabet soup agency has active nodes hoping to read the exit of your encryption
But smooth Tor ISN't perfect: by the time your dealings hits the exit node — the last dance step in front landing place at your destination server — any encryption added by Tor is removed. If it wasn't, there'd be no mode for the final website server to understand the request. Though your Information science address will be hidden by bouncing around the network, any unencrypted embodied in your request can be read.
As a termination, law enforcement agencies like the NSA and FBI, and smooth more troubling agencies abroad, have been accused of setting up slews of Tor way out nodes. As a tool so often used to commit cybercrime, you can bet Tor is a stellar target for intelligence operation services.
More importantly, though Tor can be unbeatable secure, it's just non necessary for the average web user. It may even give a false sense of security to those without an discernment of the underlying engineering.
If your online activism is putting your life at risk, we recommend exploitation Tor. Otherwise, a VPN is probably entirely you need to hide your IP.
how can i hide my phone ip address
Source: https://www.avg.com/en/signal/hide-your-ip-address

0 Komentar